As digital enterprise trends like remote and hybrid work, bring-your-own-device (BYOD), and cloud-based infrastructure evolve how devices and users interact with enterprise networks, network security is evolving too.
These days, zero trust is the big buzz in cybersecurity, discussed in cybersecurity conferences and presidential press rooms alike. Zero trust is frequently interpreted as incorporating high-friction tactics like continuous re-authentication prompts and automated logouts that add obstacles, time, and frustration to the user experience.
But leveraging zero trust principles doesn’t have to mean consigning users to a world where we spend as much time trying to access digital resources as using them. For more information, see Zero Trust Architecture.
In this post, we clear up the confusion on zero trust and discuss how a thoughtful cybersecurity team can structure a zero-trust system that keeps users and data safe, and maintain a seamless user experience.
What is zero trust?
Before you evaluate how you can best leverage zero trust principles, take a step back to define it. Zero trust is a network security framework of continuous verification, moving “defenses from static, network-based perimeters to focus on users, assets, and resources”, according to the Zero Trust Architecture paper.
Instead of letting users access the entire network when their devices are authenticated, like trust but verify or trusting a device that makes it through a firewall, like perimeter security, zero trust security tactics take the approach of never trust, always verify by tracking users and data continuously as they navigate the network.
How zero trust works today
The stereotypical zero trust strategy layers continuous identity verification and encryption techniques to protect data as it moves throughout the network, creating the high-friction environment described above.
Technologies like multi-factor authentication (MFA) are implemented to limit access and authorization, while cryptography techniques encrypt data before and while it traverses the network. Indeed, those tactics were specifically mentioned in the Presidential Executive Order on zero trust.
While these are protective actions, these tactics have significant downsides to consider.
Continuous verification with MFA, constant re-login prompts, and frequent time-outs
These tactics have an adverse effect on the enterprise user experience. Authentication slows users down from their work and forces them to have devices constantly available. These frictions multiply for single users when they leverage multiple devices (phone, laptop, or tablet), which is increasingly common in the workplace today.
Most worryingly, all these efforts can lead to “authentication fatigue,” where users are asked to authenticate so much that they no longer pay attention to the notification. This is itself a significant security gap that increases the likelihood of a breach.
Encrypting everything, always
This tactic runs the risk of over-reliance on a useful layer of security to the point of obsolescence. Already, advances in computing technology have the potential to break or severely limit encryption as we know it.
In addition, when you consider that encryption is only as secure as its keys, the ability of world legislatures to mandate back doors into end-to-end encrypted systems presents an increased likelihood of breaking the encryption and opening up attack avenues. This could leave organizations almost as vulnerable as they were before encryption.
To realize the true potential of zero trust, a more holistic, expansive, and sustainable interpretation of the principles are required.
Comprehensive zero trust
At its core, an effective zero trust strategy enables a positive user experience while ensuring a high level of security. Using analytics and automation technologies that monitor and act on suspicious behavior in the network can help reduce friction.
The following components are key to enabling a comprehensive security architecture based on zero trust principles
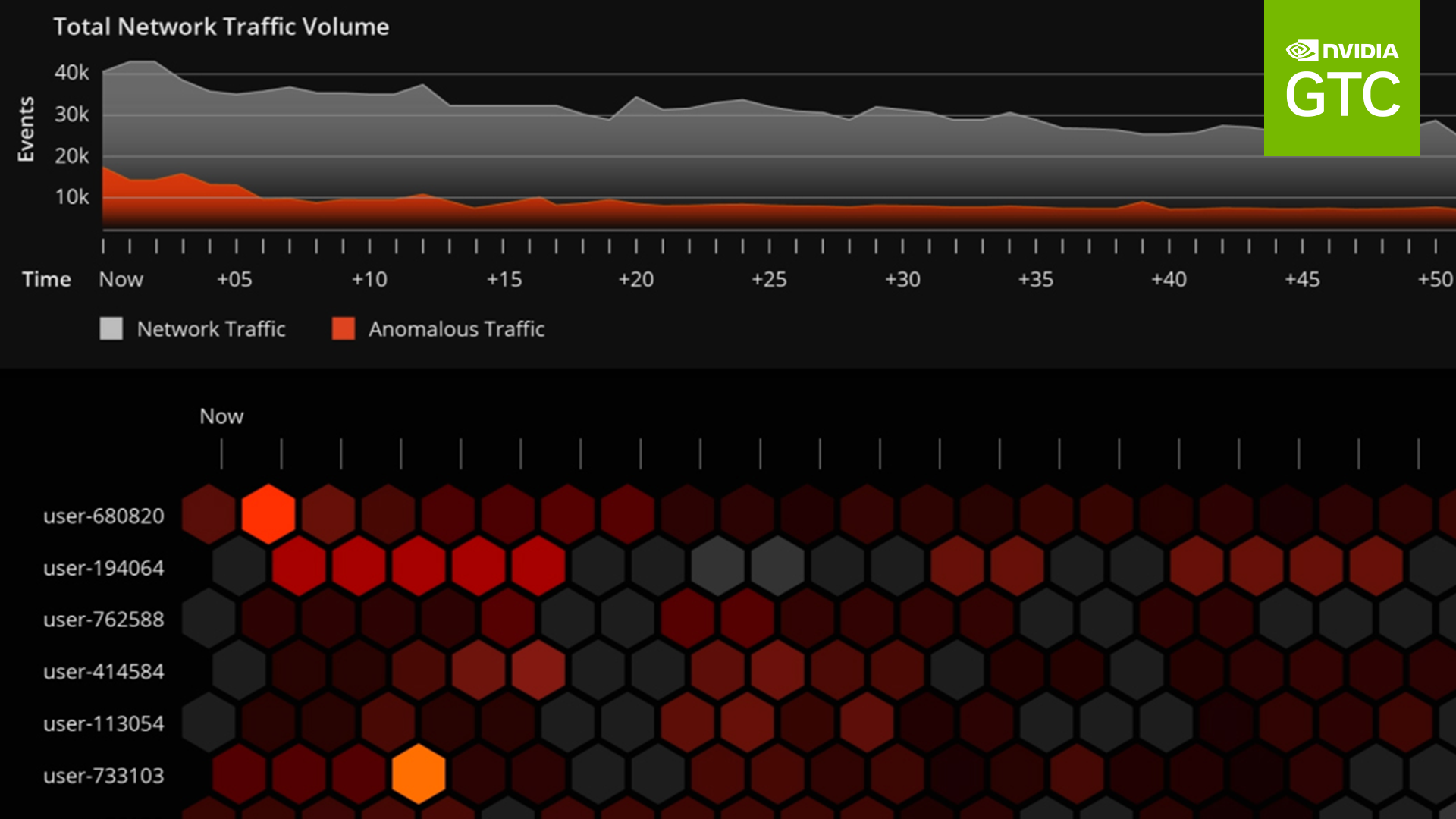
To ensure a strong authentication function, the network should be continuously monitored with automated data collection of user behavior. This data forms a real-time base for information that can be analyzed and acted upon, replacing repeated identity verification requests with actionable information.
To establish access protocols, network architects should build in User Behavioral Analytics (UBA) that can use multiple variables for context clues based on the data and learn with AI to make better and faster judgements on suspicious activity. This helps to avoid cumbersome rules in system design, and positions authentication requests as targeted access tools instead of a default.
The promise of UBA can be realized by distributing compute through the environment, leveraging logging devices, NICs, compute nodes, and storage nodes to accelerate the analytical function. For more information, see NVIDIA Morpheus Cybersecurity.
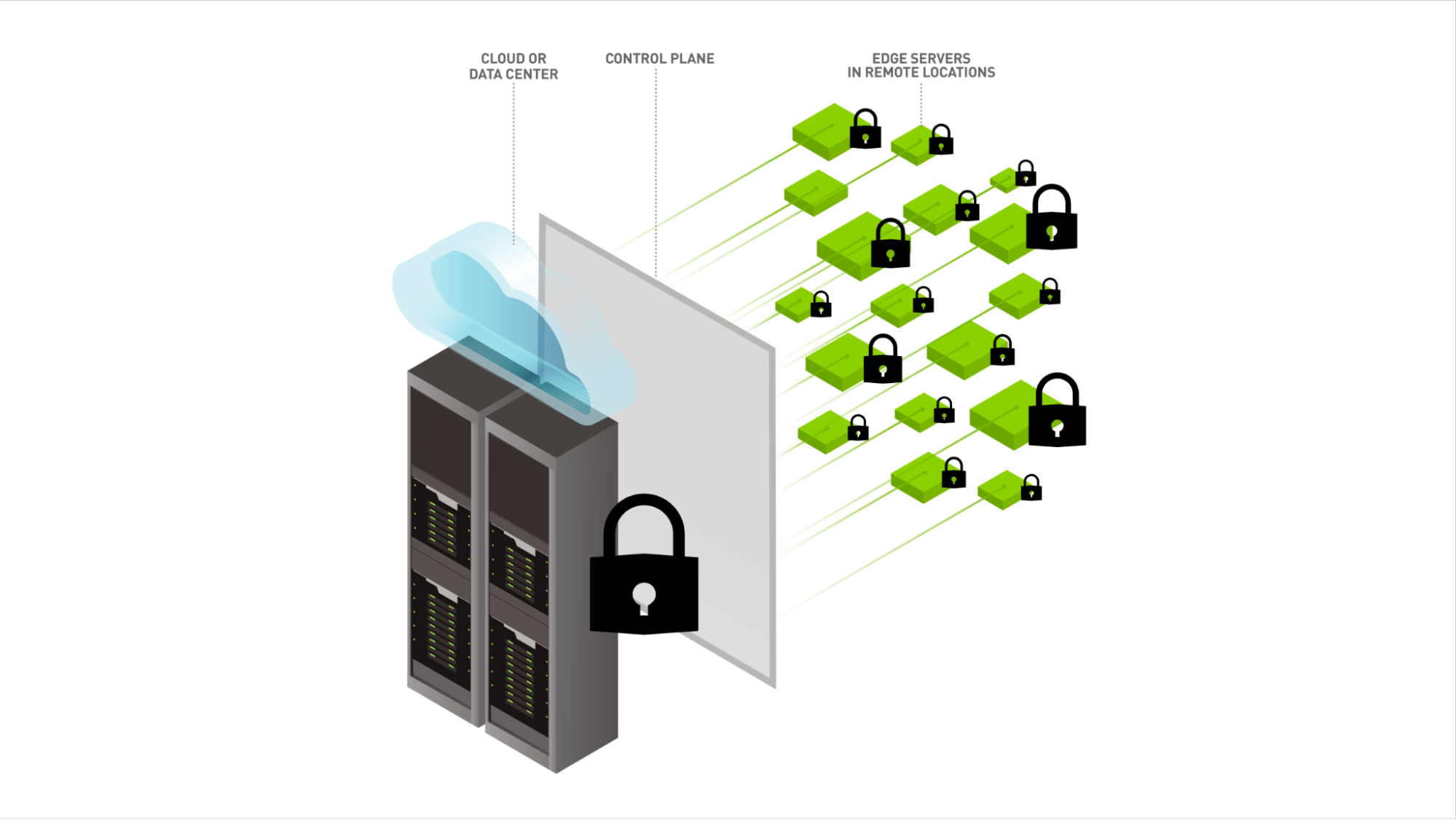
To protect data in case of a breach, systems should be architected to place defense throughout the fabric of the data center, rather than focusing on the perimeter. Network architectures often focus on preventing malicious actors from leaving the network, but that is an inverse of “perimeter security.” It’s just as important to limit lateral movement inside the network.
Encryption can help, but larger architecture network adjustments, as well as instrumentation changes, and additions should be incorporated as the primary strategy. This approach will result in orders of magnitude more data to collect, analyze and include in automated security systems.
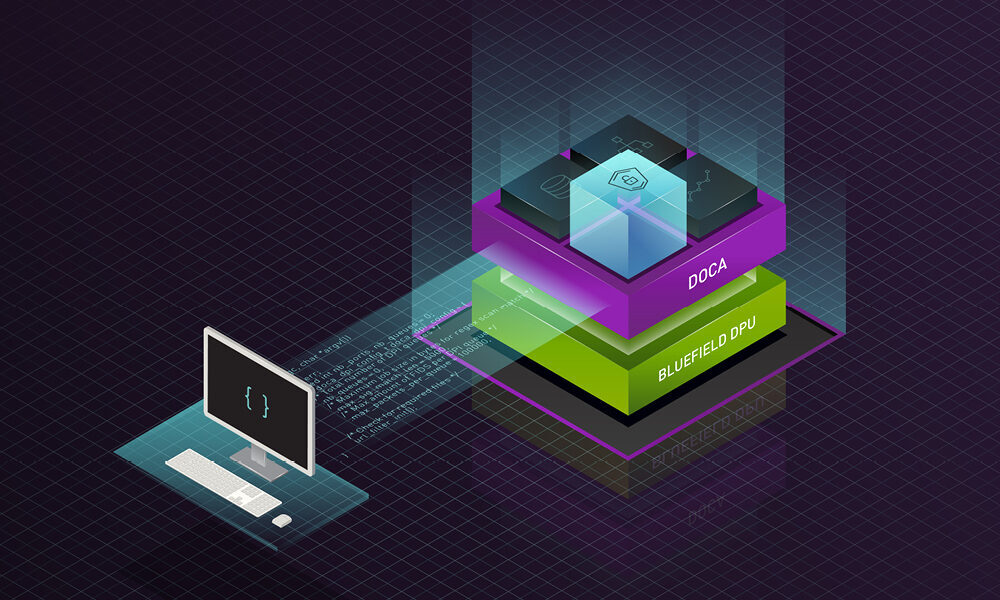
These tactics are designed to scale and evolve as the needs of enterprises do. The prospect of scaled data collection, analysis, and action with current infrastructure may sound daunting. To support the effort, the NVIDIA zero-trust cybersecurity platform combines three technologies—NVIDIA BlueField DPUs, NVIDIA DOCA, and the NVIDIA Morpheus cybersecurity AI framework—that enable development partners to bring a new level of security to data centers.
Summary
The NVIDIA zero trust platform brings the power of accelerated computing and deep learning to continuously monitor and detect threats, and isolates applications from infrastructure to limit lateral breaches, at speeds up to 600x faster than servers without NVIDIA acceleration. With this infrastructure, strong data management and AI techniques, the promise of zero trust can be realized in the next generation of cybersecurity.
To learn more about zero trust, join the Rethinking Zero-Trust: An AI-Based Approach to Cybersecurity webinar where we discuss how our zero trust platform can help address cybersecurity in the public sector.