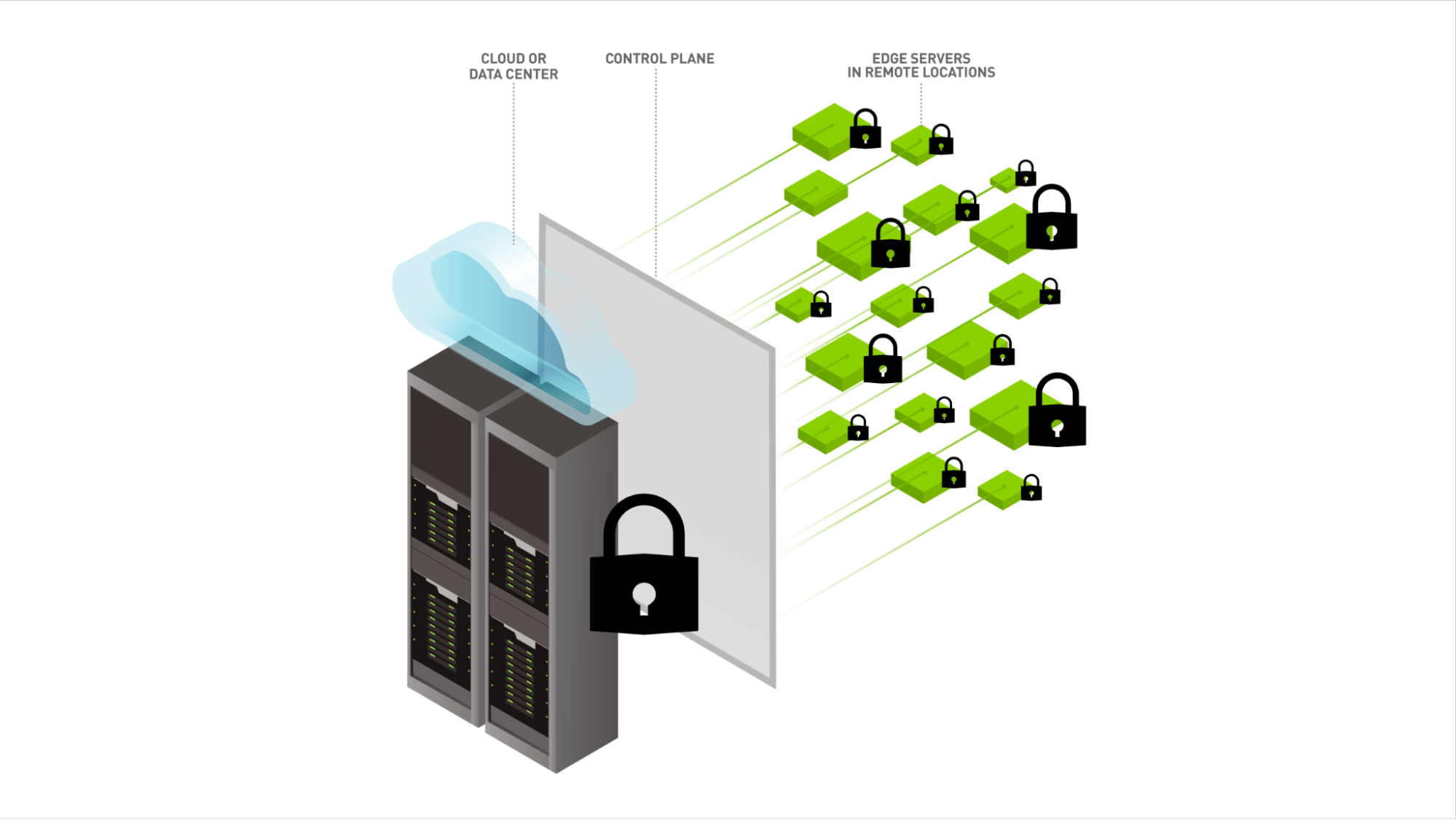
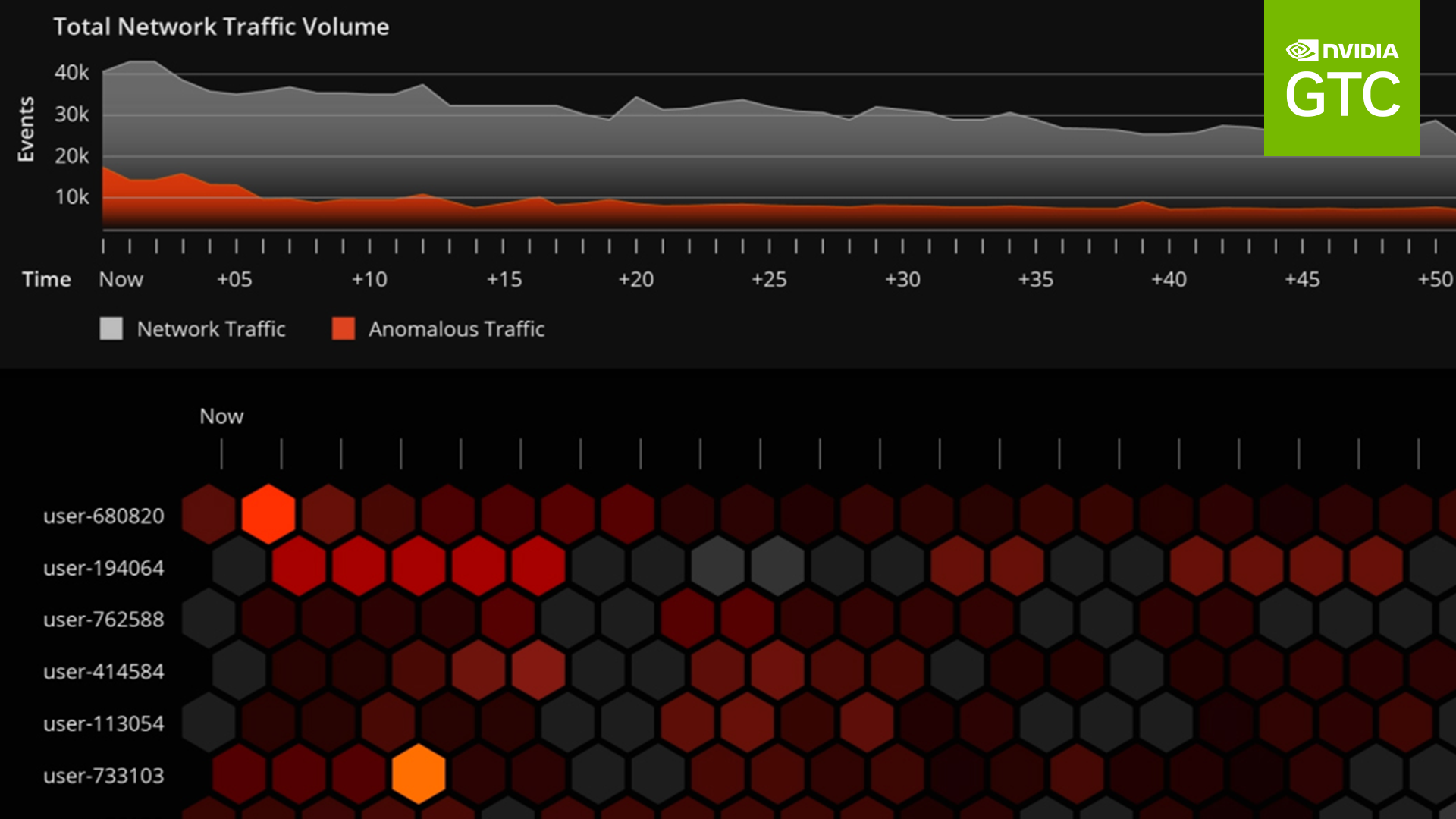
Data is increasingly being generated at remote edge locations out of reach from traditional data center solutions. To take advantage of these sources of data, companies adopt edge computing by moving computing power and storage closer to where the data is collected. This decreases bandwidth costs and latency when streaming data back to a data center or cloud. Edge computing delivers applications to customers and employees in a more cost-effective way. While there are many benefits to deploying applications at the edge, edge devices create potential entry points for cybersecurity threats not seen in a traditional data center model, such as DDoS attacks or endpoint malware.
As critical infrastructure such as healthcare, robotic manufacturing, utilities, and telecommunications increasingly incorporate AI-capable devices, edge security becomes a serious concern for society. Edge AI systems are vulnerable. They contain valuable IP and private user data that can be stolen, commandeered for other applications such as bitcoin mining and DDoS attacks, or used to manipulate critical infrastructure. Operators of edge computing have a responsibility to secure endpoints, networks, and data.
As a leader in AI computing, NVIDIA is bringing expertise to the forefront and helping customers understand how to protect valuable AI models and applications when deploying at the edge.
To understand the new approach to edge security, it’s important to compare it to the traditional security models that have been implemented in the data center.
Data Center Security
There are two initial layers of security applied in the data center—physical security and secure control over the logical network. When operating a data center, colocation, or cloud there must be a perimeter that is well-defined and controlled. Organizations have strict policies that determine who can enter the data center, ensuring no one is able to get physical access or tamper with systems.
With physical security locked down, organizations set up network controls that restrict who can connect to the data center, even limiting those on the company VPN. Companies use ephemeral jump boxes, which narrow access to the data center, leveraging keys that uniquely identify users. Network controls in the data center further limit which employees have the right to change systems and include robust logging tools ensuring all changes are recorded for audit and security responses.
Edge Computing Security
Physical Security
With edge computing sites, these security norms are flipped on their head. When designing a secure edge computing solution, organizations have to make the assumption that a malicious person could get physical access to a machine if they wanted to. For example, an edge system at a supermarket or a big-box store is often in the store manager’s office or IT closet. Much of the time, this location may not be locked and almost anyone can get to the server.
This means someone could steal the machine and take it off-site to extract sensitive data, patch the operating system in a malicious way, or even change system drivers. To counter these physical threats, stored data at the edge is encrypted and the hard drive partitioned so the boot partition is made immutable and can’t easily be rewritten or changed.
The physical system can be equipped with physical tamper detection. A Trusted Platform Module (TPM) on the system can be used to ensure secure and measured boot. This means that the firmware and kernel-mode software is checked when the system boots and it will only load if it’s signed, demonstrating that it came from a trusted source. Solutions that have signed containers add additional security checks to ensure that running applications have not been tampered with.
Zero Trust Networking
Another challenge to consider when deploying AI applications at remote locations is the network. Traditional network security is based on a concept known as castle-and-moat, where it’s difficult to connect from the outside, but there’s default trust with everyone in the network. For obvious reasons, this model breaks down at the edge where “trusted” devices can be located anywhere.
Zero Trust networking assumes no trust, even for those in the network. Instead, any access points on the network are assigned a trust policy for who, what, when, where, why, and how for the limited time needed to accomplish a specific task.
With remote management of edge systems, companies can now leverage access controls to ensure the right people have visibility to the system.
Going back to the supermarket example, typically an IT that manages the overall edge computing infrastructure decides which users have access. In this scenario, organizations can set up least privileged policies so that a user is given the least amount to do their job. This could mean some users have access to see what’s going on and view alerts, but not to make changes.
Alternatively, other users have access to deploy and manage AI applications at the edge without being able to manage the physical systems themselves. In some instances, third-party application vendors may be given access to manage applications at edge locations. Unlike a traditional data center, there may be more people who are responsible for the applications running at the edge requiring IT to create specific trust policies that limit tampering or malicious behavior.
Edge AI Security
As more AI applications are deployed at edge locations, organizations need to ensure that the security policies put in place take into consideration the changes remote environments bring.
NVIDIA has a robust security team that is continually investing in the best security standards for accelerated computing.
Other areas NVIDIA is focused on to help with edge computing security include:
AI model protection: AI models are expensive to create, and tailor to specific environments. So the owners want assurances that those models are protected at rest, in transit, and in use. To help protect these unique workloads, NVIDIA has partnered with Mitre, Microsoft, and 10 other organizations to take on machine learning threats.
Edge node security: Due to the lack of physical security for most edge computing systems, software techniques rooted in hardware security features like a secure and measured boot, remote attestation, and drive encryption are critical components of edge computing security.
Distributed device management: When deploying edge systems at hundreds, or even thousands of locations, centralized management with granular access controls is critical for any edge security model.
Edge to cloud connection security: A secure provisioning process to add new nodes at locations at the edge ensures that only systems with administrator approval are added. Additionally, setting rules for communication between nodes at the edge and the cloud management platform protects and isolates data.
Distributed analytics security: For AI models that use multiple connected systems for analytics, ensuring authenticated and encrypted communication between those systems adds an important additional layer of security, especially for organizations collecting and analyzing sensitive or regulated data.
To stay up to date with the latest security considerations for edge computing be sure to subscribe to NVIDIA edge computing news. For those looking to learn more about other considerations when deploying edge computing, register for the Top Considerations for Deploying AI at the Edge whitepaper.