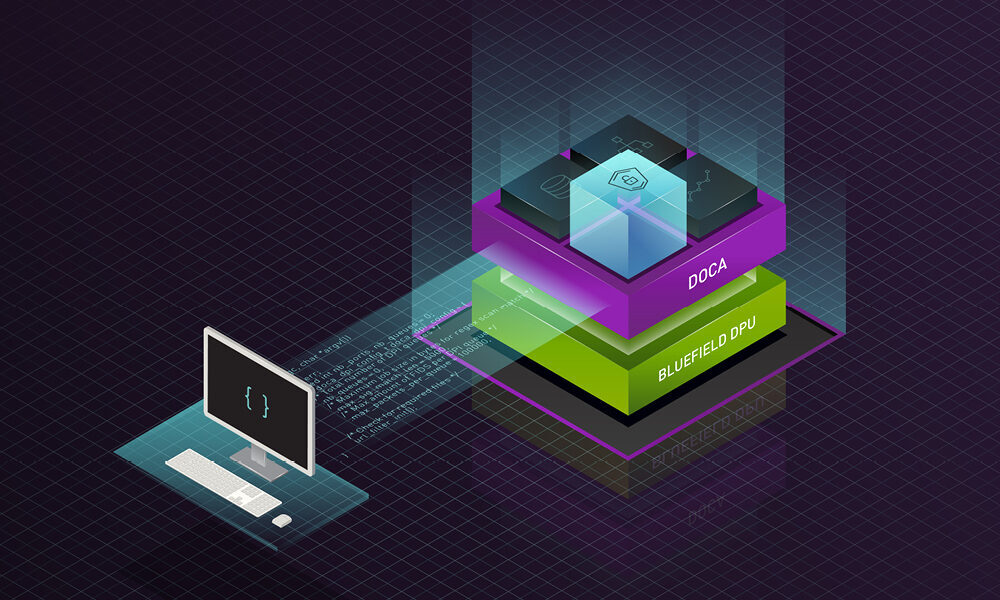
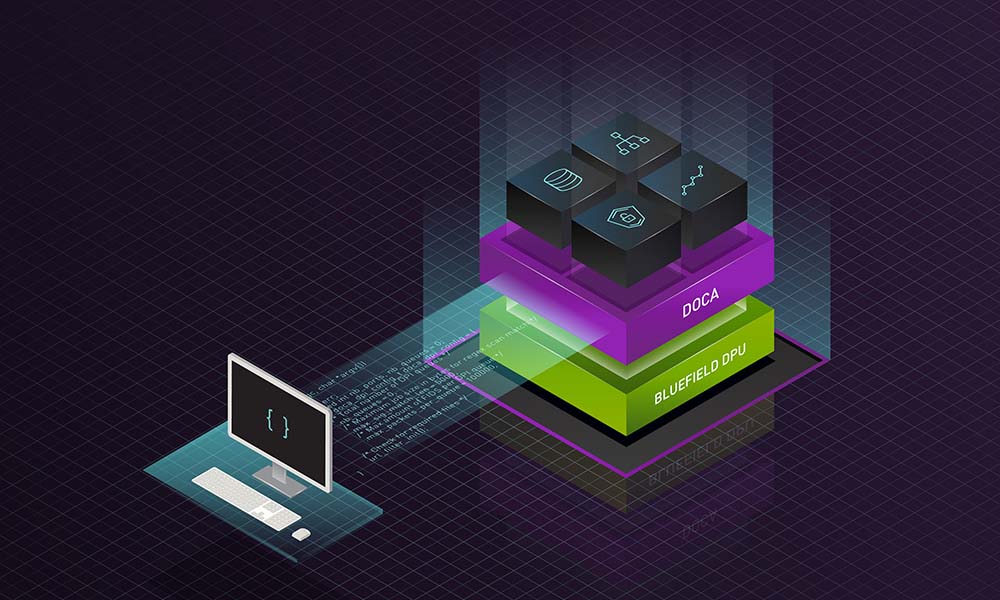
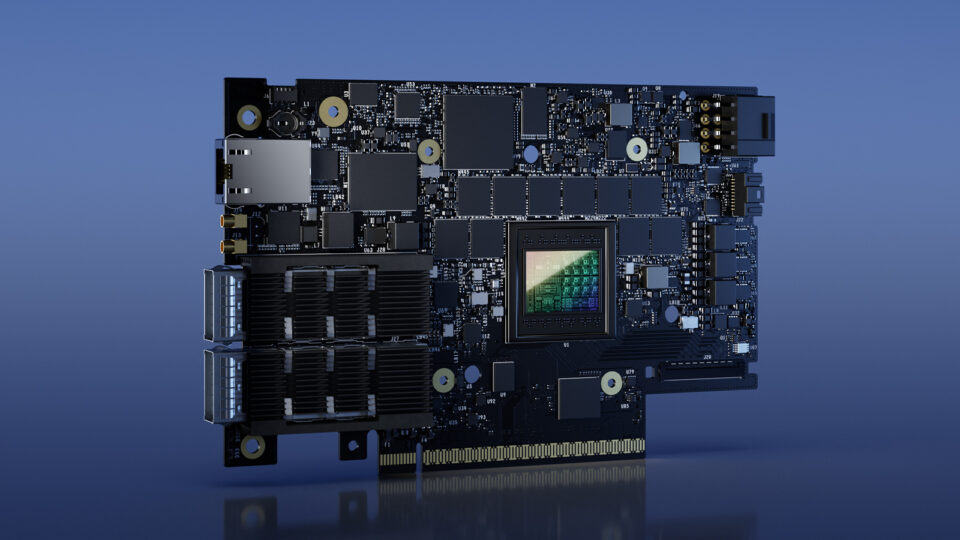
Today NVIDIA introduced the NVIDIA DOCA 1.2 software for NVIDIA BlueField DPUs, the world’s most advanced data processing unit (DPU). This latest release, scheduled for late November, builds on the momentum of the NVIDIA DOCA early access program to enable partners and customers to accelerate the development of applications and holistic zero trust solutions on the DPU.
New authentication, attestation, isolation, and monitoring features make BlueField the ideal foundation for a zero-trust, distributed security platform.
Previously, perimeter security was sufficient to protect from external threats, because users, devices, data, and applications inside the data center were implicitly trusted. But with cloud, private cloud, software as a service, bring your own devices (BYOD), and users downloading numerous apps into the data center, this implicit trust is no longer warranted or acceptable.
Therefore, the zero trust model realizes that resources inside of the data center cannot be trusted any more than those outside. Zero trust starts with the assumption that all users, devices, applications, and data, even those inside the network perimeter, are untrusted.
Zero trust calls for enterprises to leverage micro-segmentation and granular authorization enforcement based on the user. Analyzing the users’ rights, locations, need to access data, and behavioral history determines whether to trust a user, device, or application to access a particular resource. It monitors the behavior of every user, application, and server, and checks traffic on every part of the network using technologies:
- Multi-factor authentication
- Role-based access controls (RBACs)
- Next-generation distributed firewalls
- Deep packet inspection
Users and devices are authenticated to make sure that only authorized users have access while encryption ensures privacy. Zero trust calls for granting users only the access needed to accomplish each specific task and no more.
A zero-trust cybersecurity model recognizes that everyone and everything, both inside and outside the network, must be authenticated, monitored, and segmented. And even once authenticated, all actions should be isolated while protecting data in-transit and at-rest with encryption to minimize the blast radius of unauthorized data access when security is compromised.
BlueField DPUs redefine the secure perimeter with a best-in-class foundation for zero trust protection. The DPU enables network screening with encryption, granular access controls, and micro-segmentation on every host and for all network traffic. BlueField provides isolation, deploying security agents in a trust domain separate from the host domain. In the event a host is compromised, this isolation prevents the malware from accessing the security software, helping prevent the attack from spreading to other servers.
BlueField DPU and NVIDIA DOCA bring zero trust to all layers of the data center
BlueField DPUs and NVIDIA DOCA offer a foundation for zero trust. Starting from a hardware root of trust to ensure the integrity of the DPU itself, we can add trust to every layer. This includes bringing attestation, authentication, and monitoring to every single touchpoint of computers, applications, and data, including servers, containers, storage, network infrastructure, and, of course, people.
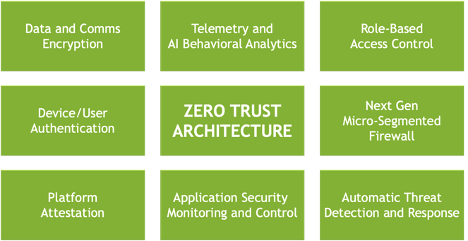
BlueField DPUs and NVIDIA DOCA provide the foundational platform for partners and customers to build holistic zero-trust solutions. The BlueField DPU delivers three critical capabilities as part of this foundation including:
- The ability to authenticate the platform, including:
- DPU secure and measured boot based on a hardware root of trust.
- DICE-based platform and remote attestation of the DPU software. DICE is a family of hardware and software techniques for hardware-based cryptographic device identity, attestation, and data encryption.
- Tools to accelerate authentication, access control, and encryption.
- Offload authentication and attestation using public-key cryptography.
- Control access to assets and data with software-defined, hardware-accelerated micro-segmentation and stateful connection tracking.
- Accelerate encryption of data on the wire and at rest.
- Implement a stance of “still don’t trust—verify always.”
- Monitor network traffic and report suspicious activity with NVIDIA DOCA telemetry.
- Isolate software in a domain separate from the CPU/application.
- Shield host applications from corruption or malicious modification.
The previous notion of “trust, sometimes verify” now becomes “don’t trust, authenticate, and attest and then still don’t trust, so always monitor and verify.” The core assumption is that any asset could become compromised even after authentication and thus continuous activity monitoring is required to protect users, devices, and data.
The BlueField DPU enables this at the lowest level by providing hardware root of trust with unique device IDs. Then, it performs a measured, secure boot that verifies that all the software running on the DPU is signed and authenticated.
Measured boot addresses the problem that a boot image can be properly signed and authenticated, and then the actual boot process is subverted to load different or additional code. Both secure and measured boot rely on the hardware root of trust as a starting point to extend the chain of trust. Measurement calculates a secure hash of the signed image and then measures that it is indeed the image that was loaded during the secure boot process.
After the integrity of the DPU is attested, BlueField can accelerate public key/private key authentication and extend the chain of trust to other applications, devices, and users.
BlueField also acts as an accelerated SDN platform to limit each application or user’s access to assets using role-based access control (RBAC) and micro-segmentation. For example, a containerized app that must analyze data on one storage device and pass it to a user can be put on its own network segment. There, it can only see that storage device, that user, and nothing else. The use of security groups, network micro-segmentation, and dynamic RBAC prevents the spread of any malware through internal East-West traffic.
On the “still do not trust” front, BlueField accelerates the TLS and IPsec encryption as well as storage encryption. This now makes it possible for encrypted links to operate at 200 Gb/sec with zero CPU load. The implications are that encryption at multiple layers, which are always desirable in a zero-trust framework— now can be performed much more efficiently.
This makes encryption practical for all servers and all network traffic, where previously, it was too computationally expensive to implement except on a few web and VPN connections. With all network connections and storage encrypted, any adversary that does break into the network is unable to access data.
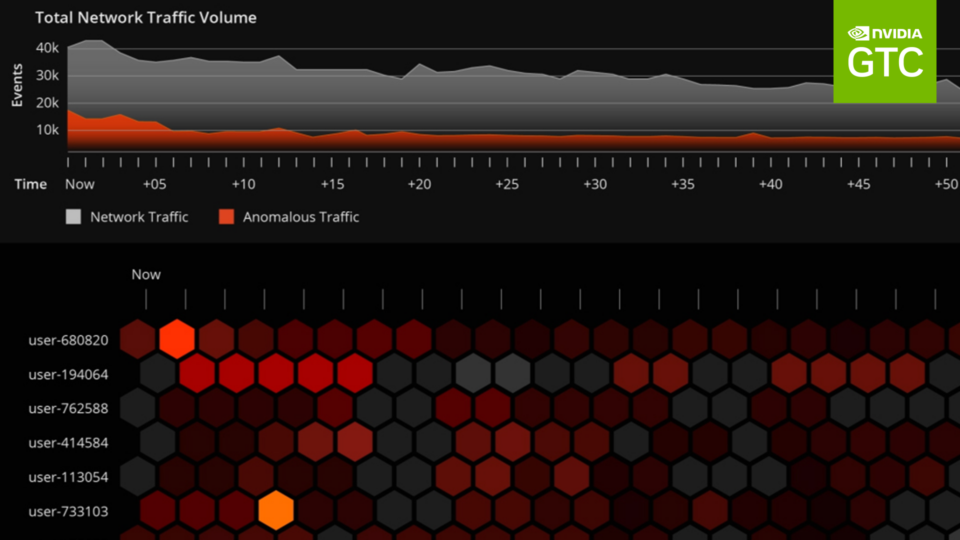
BlueField offers continuous monitoring of everything by leveraging the DPU’s built-in telemetry and alerting SIEM and XDR systems when suspicious activity occurs. The network telemetry can be fed into NVIDIA Morpheus, an AI-accelerated, scalable, cybersecurity framework. This allows partners to perform scalable AI malware detection, IDS/IPS, and auto-quarantining of compromised assets.
NVIDIA DOCA plus Morpheus can also use AI to identify non-malicious but serious issues such as misconfigured servers and out-of-date software. It can even detect cases where sensitive information—such as passwords, credit card numbers, or medical information—is being transmitted in the clear when it should be encrypted.
Now, when the inevitable cyber breach happens, multiple layers of protection limit the blast radius:
- The DPUs protect and attest to system integrity, isolating threats and protecting security software agents.
- An infected server or VM only has access to only a few other assets thanks to RBAC and micro-segmentation.
- Compromised applications are identified with App Shield.
- NVIDIA DOCA telemetry working with Morpheus detects suspicious network traffic.
- Abnormal traffic flows are blocked by leading firewall software running DPU-accelerated security and without any performance or service degradation.
- Valuable information is encrypted both in flight and at rest.
By starting with the assumption of zero trust everywhere, NVIDIA DOCA and the DPU act as the foundation for security applications to safeguard all assets, everywhere.
Summary
A modern approach to security based on zero trust is critical to securing today’s data centers, since activity inside of the perimeter can no longer automatically be trusted as secure.
This is even more important at the edge, because data centers are no longer just huge facilities with gates, guards, and guns. At the edge, there are tiny data centers in factories, robots, cars, stores, and radio towers each containing valuable assets.
However, with physical access possible, these cannot be adequately protected by traditional firewalls. So the DPU starts from a hardware root of trust and builds security layer by layer and limits network access—protecting users, devices, data, and applications, which all meet in the data center.
BlueField DPUs and the NVIDIA DOCA software stack provide the ideal open foundation for partners to build zero-trust solutions and extend them to all parts of the network, to address the cybersecurity of the modern data center.
Learn more about enabling zero-trust security with NVIDIA DOCA
Apply for the NVIDIA DOCA Early Access program
Register for the North American DPU Hackathon
Take the Introduction to NVIDIA DOCA for the BlueField DPU course
Download the App Shield solution brief
Read how NVIDIA creates a new zero-trust cybersecurity platform