Securing the private 5G and applications at the edge comes with many challenges. Sophisticated AI– and ML-based attack campaigns require security to respond in real time.
Palo Alto Networks’ security platform has been incorporating ML and AI technological breakthroughs over the years to ensure that real-time ML capabilities and AI-driven incident responses are autonomous.
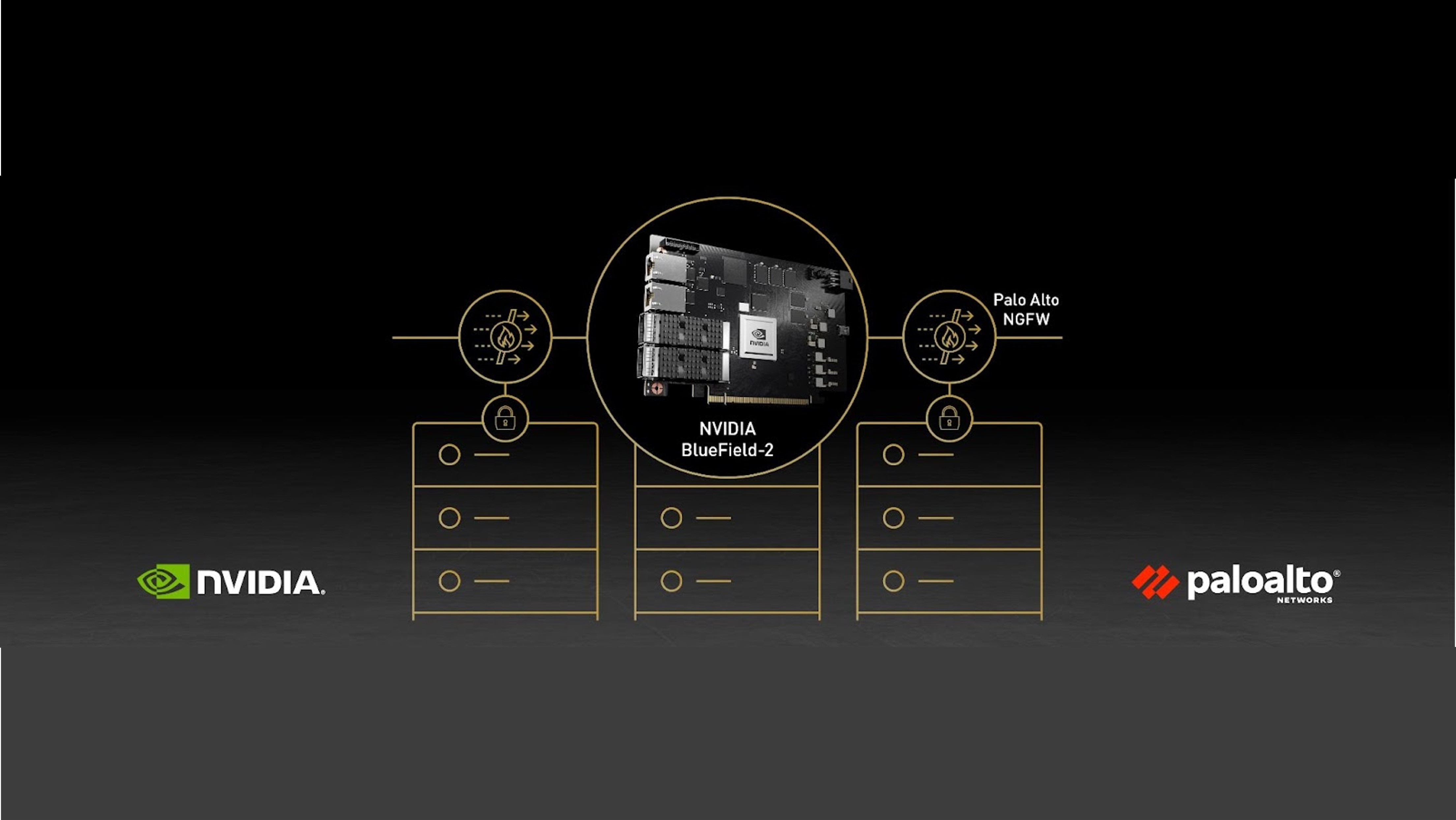
When teams from Palo Alto Networks and NVIDIA collaborated to build Intelligent Traffic Offload (ITO), our purpose was clear: to enable any enterprise to embrace 5G without compromising security over performance and efficiency. We created ITO as a foundational solution that helps establish a fast and secure private 5G infrastructure for modern enterprises.
Data processing units (DPUs) are critical components within the edge computing AI and ML infrastructure, hyperscale telco cloud, and any cloud that offers IT, OT, or IoT networks and services. Enterprise customers use ITO to scale security capabilities and increase overall firewall throughput by at least 5x.
We are bringing multiple enhancements to ITO to give you more options, ease of deployment, and higher performance, including the following:
- New support for NVIDIA BlueField-3 DPUs
- Expanded deployment modes with layer-3 routing capabilities
- Network Address Translation (NAT)-based offloads
While the static and dynamic routing offers expanded options for deployment, the NAT-based offloads help you secure the Internet perimeter to shield end-user identities and offload traffic at the same time.
ITO now on NVIDIA BlueField-3
In addition to the existing NVIDIA BlueField-2 DPU integration, we are expanding our offering to include support for NVIDIA BlueField-3 DPUs.
Our ITO solution accelerates Palo Alto Networks’ VM-Series Virtual Next-Generation Firewall (NGFW) with the NVIDIA BlueField DPU to significantly increase the throughput while substantially reducing infrastructure costs.
ITO enhanced options: L3 support
When we launched ITO, we supported the vWire mode of firewall insertion. This means that the firewall does not perform any switching or routing functions. It just acts as a bump in the wire. This is beneficial for specific environments where no routing or switching is needed or if the firewall gets all traffic from a singular L3 domain.
The new layer 3 mode really expands your capability of taking advantage of security within your data centers, relying on firewalls to both switch and route traffic to network domains.
Figure 1 shows how the packet flow works in layer 3 mode.
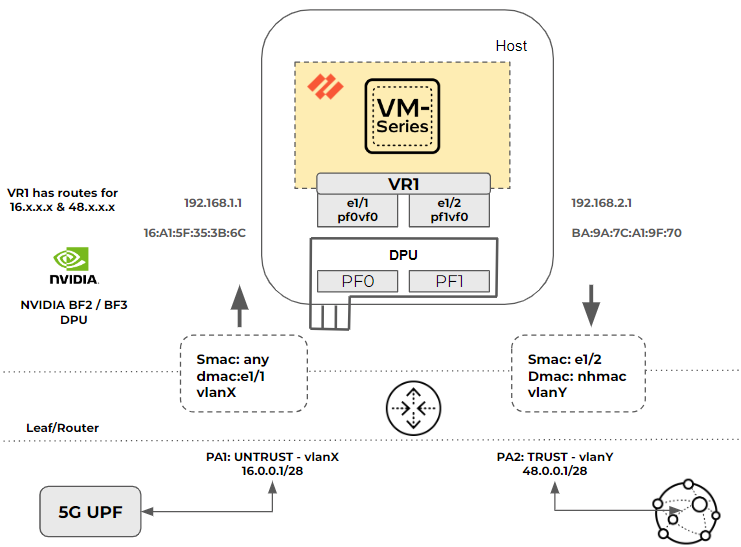
In Figure 1, the packet flow has the following characteristics:
- Interface e1/1 and e1/2 are configured in Layer 3 mode.
- VR1 is configured with static or dynamic routes to the 5G layer 3 router or a UPF and to the Internet peer router.
- Tagged and untagged traffic are supported. The router and DPU or NIC can be in access or trunk mode.
This is the packet flow process for Layer 3 mode:
- The packet is sent from the 5G UPF (Layer 3 router) to the Layer 3 Leaf/Router.
- The packet arrives at the router port PA1 connected to DPU and SmartNIC PF0 and programmed to add a
vlanXtag to the packets. - The packet arrives at DPU port
pf0vf0and is delivered to the VM-Series with or without removing the VLAN. - The firewall is running in L3 mode. It finds the packet’s next hop and its MAC address.
- The firewall updates the DPU and SmartNIC through gRPC with the new destination MAC and
vlanY, if required. - The tagged packet with
vlanYarrives at router portPA2from the DPU and SmartNIC portPF1. - If the packet was untagged, the router port
PA2may add tagvlanY. - The packet is sent to the next-hop address and delivered to the Internet peer. In the case of dynamic routing, with any route update, the VM-Series updates the DPU with the new next-hop MAC address.
ITO enhanced options: NAT support for vWire and L3
Typically, in 5G deployments and certain hyperscale enterprise environments, the PAN VM-Series virtual NGFW secures the Internet perimeter or north-south traffic. In such deployments, you can take advantage of our NAT mode to ensure that end-user devices are not exposed to the Internet.
We are bringing NAT support with ITO capabilities in both vWire and the Layer 3 mode of deployment. You can now configure multiple modes of NAT with IPv4, such as source NAT with dynamic IP address and port translation, destination NAT port translation, and forwarding.
Figure 2 shows how this works from a packet flow point of view.
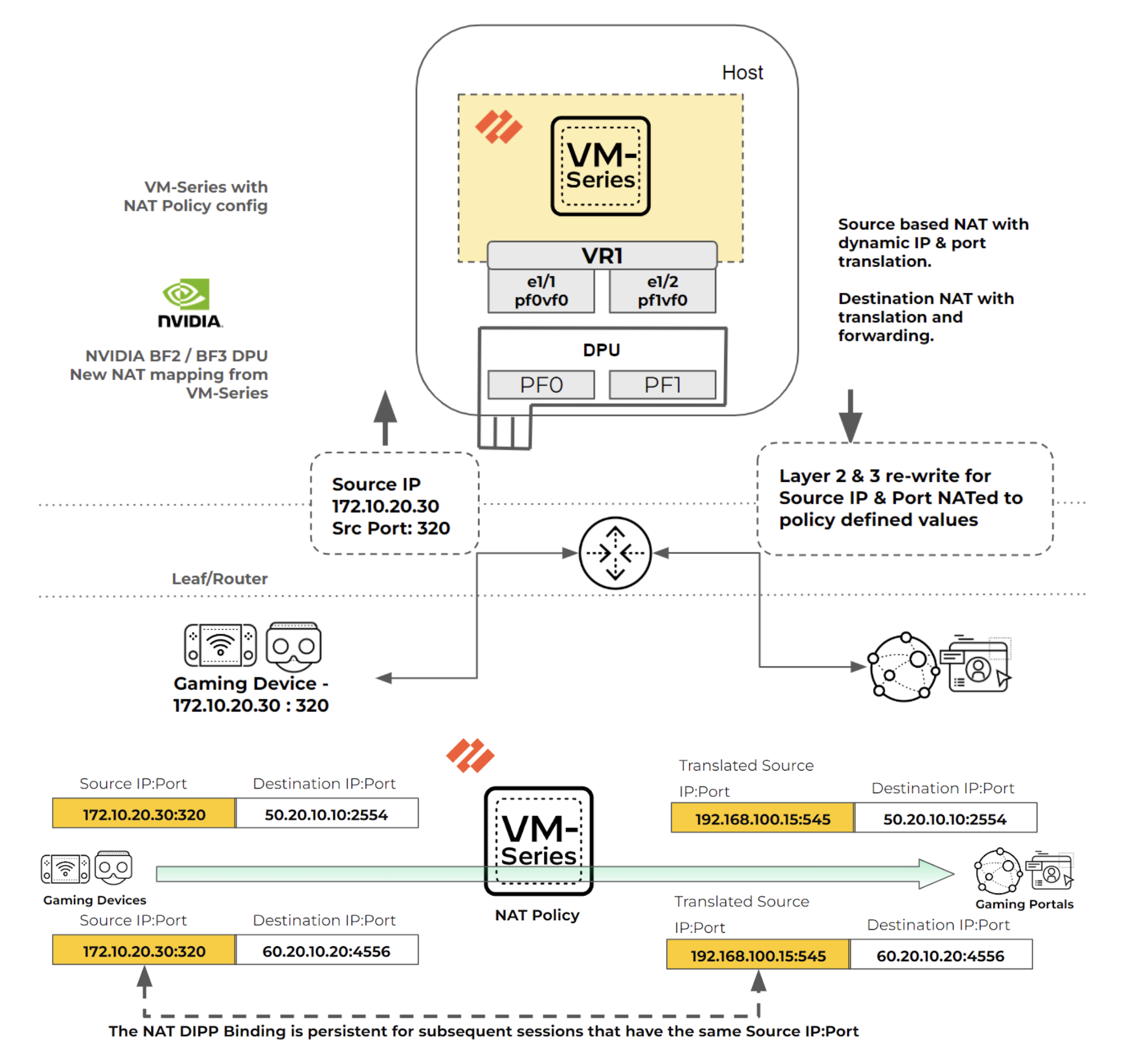
Here’s how the NAT policy is configured:
- VM-Series has the NAT policy configured to perform source NAT for IP and port to dynamic IP and port mapping.
- The NAT policy defined can also perform destination IP and port translation and forwarding.
This is the packet flow process when a NAT policy is configured:
- The packet is sent from the 5G device through the 5G UPF or Layer 3 router with a source IP address and port 172.10.20.30:320.
- The packet arrives at the VM-Series, where the NAT policy is defined to do source NAT to dynamic IP address and port translation. The source IP: Port 172.10.20.30:320 is translated to 192.168.100.15:545.
- The VM-Series does a layer 2 and layer 3 re-write on the packet based on the defined NAT policy, which can be source NAT with dynamic IP address and port translation or destination NAT with port translation and forwarding.
- The VM-series updates the DPU and SmartNIC through gRPC with the NAT translation.
- The SNAT DIPP maintains persistence by retaining the binding of a private source IP address and port pair to a specific public (translated) source IP address and port pair for subsequent sessions with the same original source IP address and port pair. In this case, 172.10.20.30:320 and its translated 192.168.100.15:545 address are persistent for multiple destination IP address ports.
Conclusion
By taking advantage of the enhanced features of ITO, you now have expanded options to deploy VM-series NGFW in either vWire or layer 3 mode. You can continue to use NAT capability on VM-Series with ITO seamlessly. These features are also available on the NVIDIA BlueField-3 DPU where you can unlock further benefits of higher throughput with at least 5x better security performance.
Together, Palo Alto Networks and NVIDIA are bringing zero-trust security to enterprises, with no compromises on performance and efficiency. Get started with Intelligent Traffic Offload on BlueField DPUs today with the ITO deployment guide. Take the next step by contacting your NVIDIA sales representative.