Authentication and Validation of Binaries#
All firmware binaries and calibration data (i.e., BCTs, DTBs) loaded by BootROM, MB1, MB2, and Partition Loader are validated, authenticated, and optionally decrypted. The following category of binaries go through this process:
BPMP related firmware binaries including MB1, BPMP_FW, and associated calibration data
PSC related firmwares including PSC-BL1 and PSC-FW
CCPLEX related firmware binaries including MB2, ARM Trusted Firmware, Secure OS, partition table, and associated calibration data
CCPLEX virtualization binaries including Hypervisor, servers, Partition Loader, and associated calibration data
Auxiliary firmwares including FSI, DCE, RCE, PVA, APE
Key IST firmware binaries and calibration data
Runtime IST firmware binaries and calibration data
SC7 support binaries
Guest OS binaries including kernel and associated calibration data
In T264, BCH group can hold up to eight (8) OEM signed binaries signature or up to two (2) NV signed binaries signature.
NV signed grouping is not implemented in software. For OEM signed binaries grouping, there is a condition that all binaries in the group must be loaded by same boot component.
A BCH has an array of eight (8) OEM signed components and has the following details about the binary:
Destination load address.
Location of binary on storage.
Size
Version and Ratchet level
Encryption parameters
Hash Value.
Note
Provision for destination load address and location on storage are not supported by all boot components. The ones that are supported by all boot components are:
Size
Version and ratchet level
Encryption parameters
Hash values
For more information about BCH refer to Grouping of Boot Images.
Dual Authentication of Firmware#
MB1 firmware and BPMP firmware are delivered in binary form and are signed with the NVIDIA and OEM RSA keys. As a result, two validation steps are required:
Authentication and validation with the OEM key
Authentication and validation with the NVIDIA key
Recovery Support#
For authentication and validation information consult Security Framework.
SecureOS#
The SecureOS (TOS) runs in EL3 mode and provides SecureMode support.
Hypervisor-based Flow#
The hypervisor-based flow is as follows:
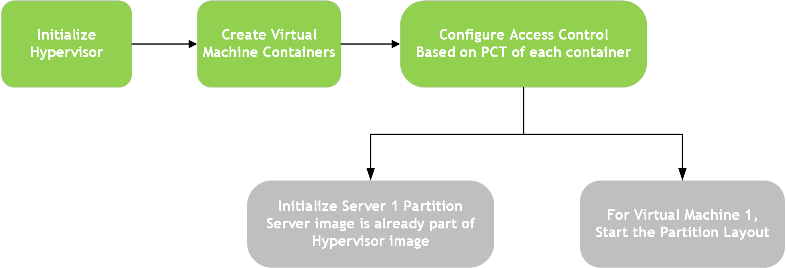
Virtual Machine#
The Virtual Machine (VM) is an emulation of a native system. It is a software container that functions as an independent system with its own dedicated hardware and operating system, called guest OS in the context of Hypervisor.
Partition Loader#
The PartitionLoader (PL) is a special purpose boot loader image embedded into the Hypervisor. It acts as Virtual boot ROM for the virtual machine.