Persistent Key Object Support
NVIDIA DRIVE OS Security Services provide the ability to persistently store custom key objects on dedicated secure storage media. The format of the objects adheres to the PKCS#11 specification. The NVIDIA DRIVE OS PDK provides users the ability to generate customized wrapped PKCS#11 Key Objects and reference code that demonstrates how to provision said objects into the dedicated secure SPI-NOR hardware.
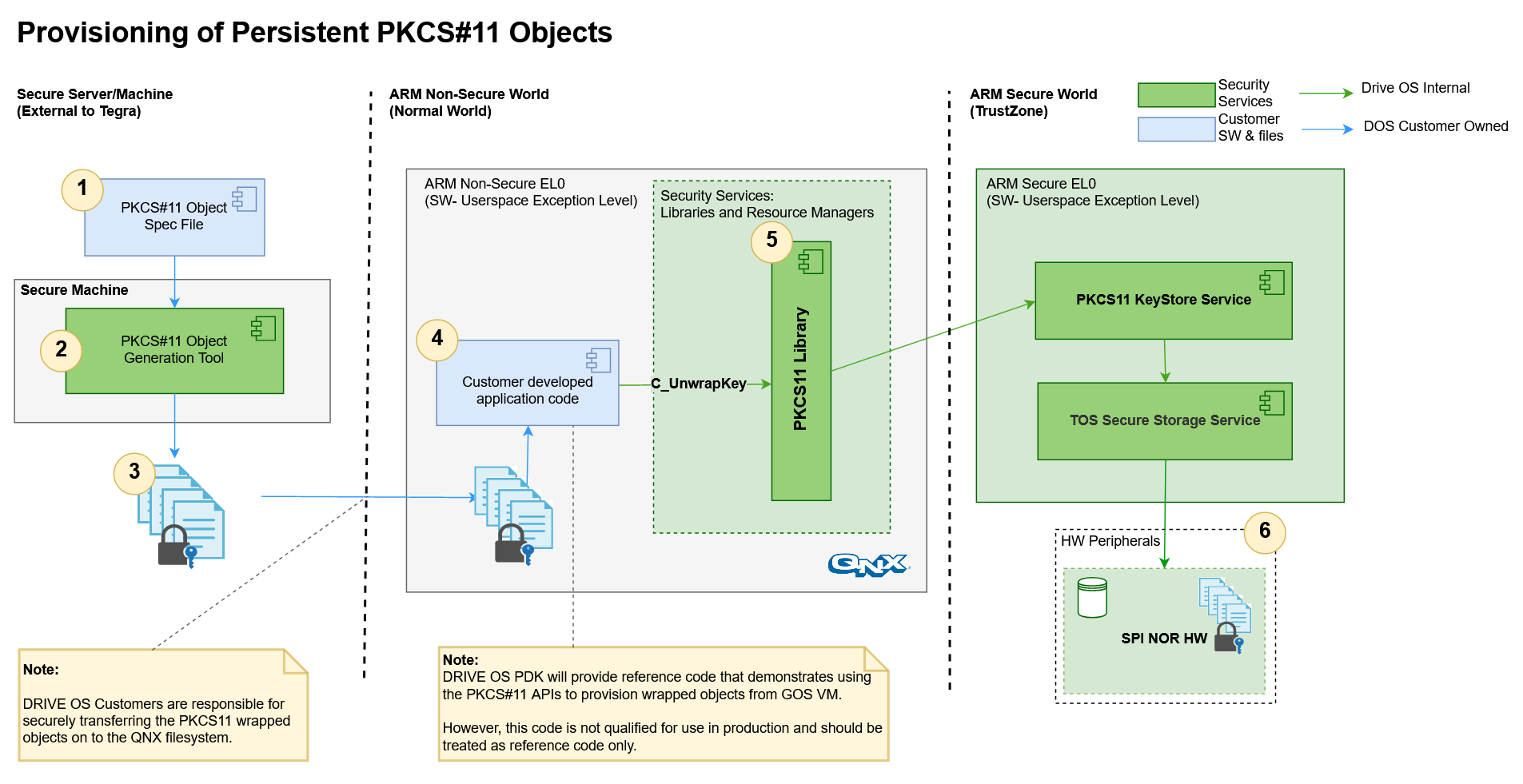
The following section describes the annotations in the “Provisioning of Persistent PKCS#11 Objects” image above.
PKCS#11 Object Spec File(s)
These files are the input to the PKCS#11 Object Generation Tool that specify secret key material and metadata associated with each key object. These input files must be generated in a secure environment to prevent disclosure of secret key material and associate metadata.
Refer to the Generating PKCS#11 Key Objects section for more details.
PKCS#11 Object Generation Tool
The PKCS#11 Object Generation Tool takes the inputs from the PKCS#11 Spec files and a secret key (KEK0) to generate binaries associated with each key object.
Refer to the Generating PKCS#11 Key Objects section for more
details.
The PKCS#11 Object Generation Tool is implemented in a way to facilitate deployment on custom HSM solutions. By default, all cryptographic primitives use openSSL but are abstracted in a separate source file and can be easily replaced with HSM-specific constructs.
PKCS#11 Key Object format is not guaranteed to be forward compatible and is subject to change in subsequent releases. The PKCS#11 Object Generation Tool ensures that the generated object format is aligned with DRIVE OS internal services.
Please consult with an NVIDIA representative before making changes to the object format. Any modifications to the PKCS#11 Object format in the generation tool may result in a failure during key object provisioning.
Wrapped PKCS#11 Key Objects
These are the binary outputs of the PKCS#11 Object Generation Tool. These wrapped objects are authenticated and encrypted and must be securely transferred over to the target file system where the application will access them.
Application to provision PKCS#11 Key Objects into Secure SPI-NOR hardware
Once the binary output files generated using the PKCS#11 Object Generation Tool are moved over to the Guest OS filesystem, and application must read these binaries and provision them into the Secure SPI-NOR hardware using the following PKCS#11 API:
C_UnwrapKey()Refer to the Provisioning PKCS#11 Key Objects section for more information.
PKCS#11 Library (QNX)
The user-space library that exposes Security Services to applications in the QNX Guest OS. Refer to the PKCS#11 Interface for a detailed description and documentation.
Secure SPI-NOR Hardware
The dedicated secure storage media that stores the key objects persistently. This is the destination of the UnwrapKey operation.
Confidentiality, Authenticity and Integrity
The secure storage media, along with its software driver, provides confidentiality, authenticity and integrity for the objects stored using device-specific keys. Attackers cannot read out any part of the objects in plaintext. When there is tampering against the media, errors are returned to the PKCS#11 library.
Rollback Detection
The secure storage media, along with its software driver, provides rollback attack detection for the stored PKCS#11 Key Objects. When there are rollback attacks against the media, errors are returned to the PKCS#11 library.
SPI Error Reporting
When uncorrectable errors happen during Secure SPI-NOR data transfer through SPI bus, these errors are reported to FSI.